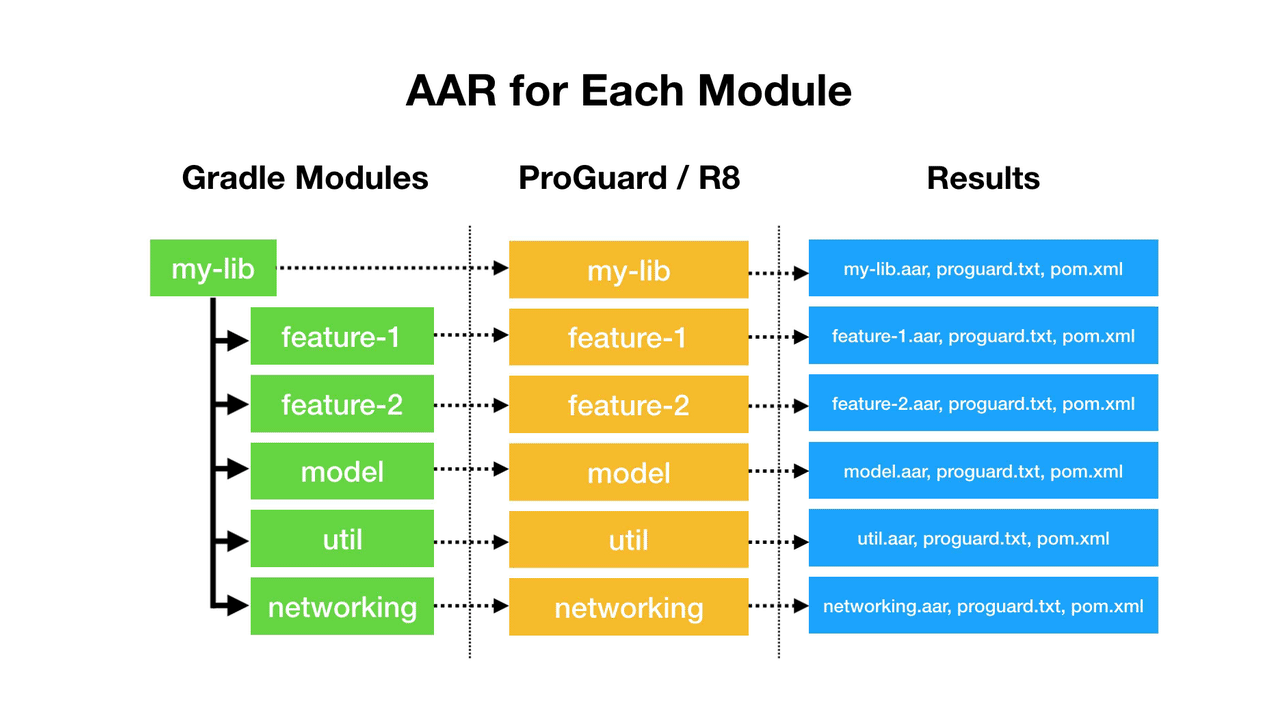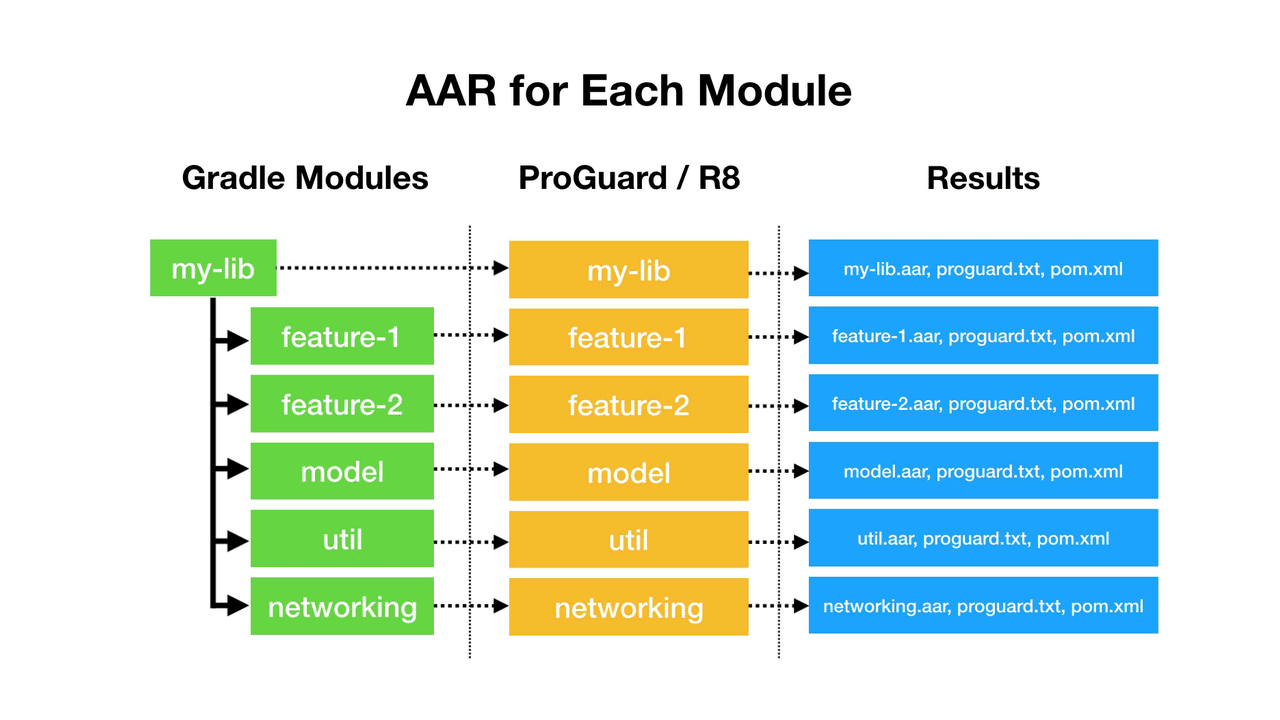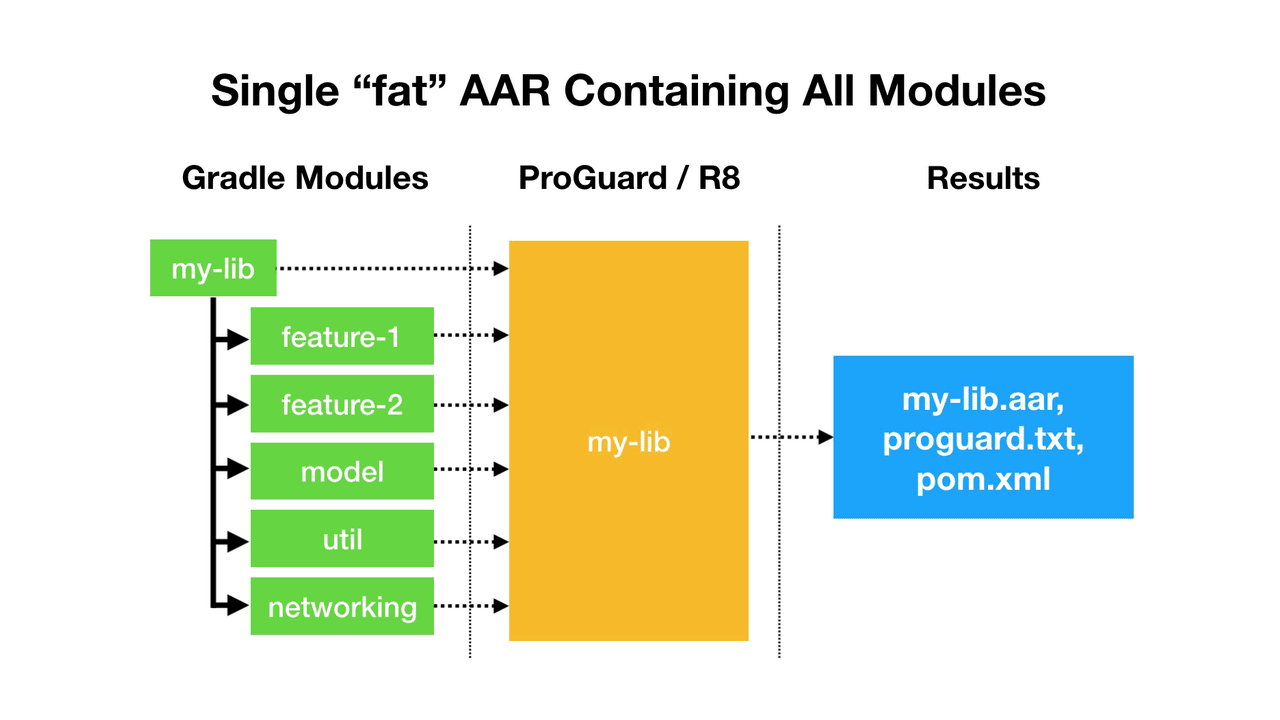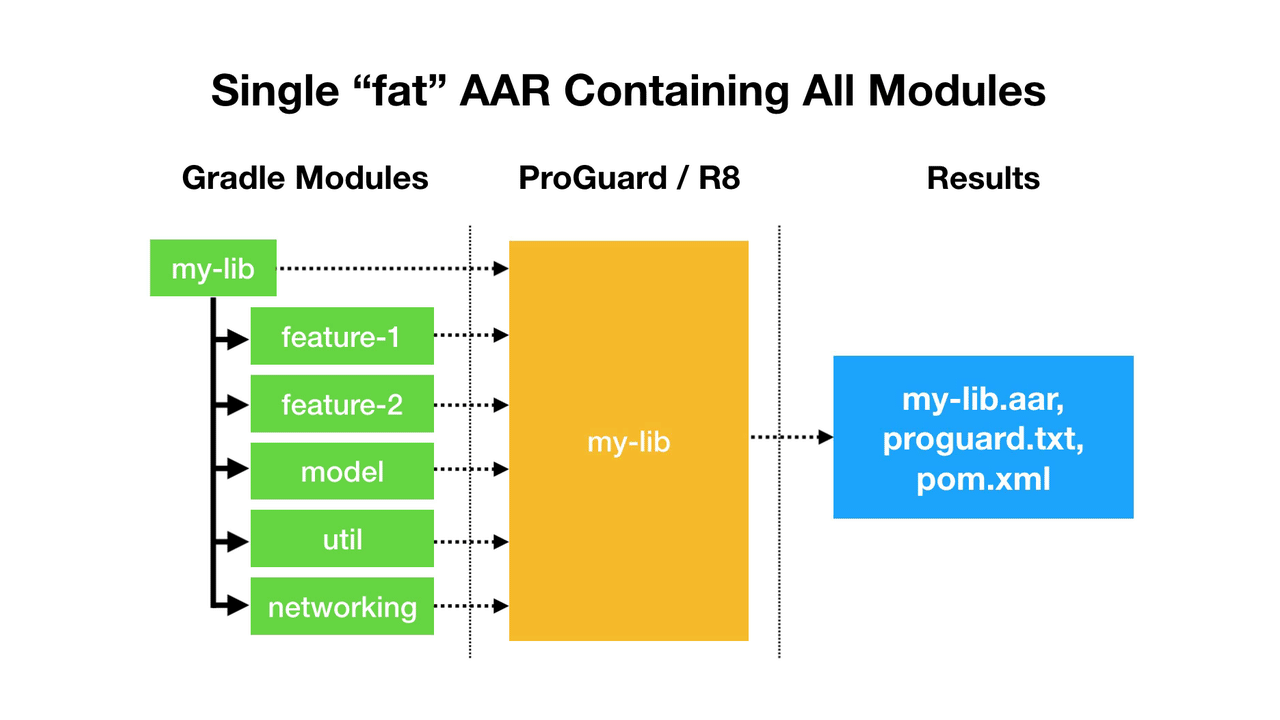
Users Say: “Biometric…🤷♂️🤷♀️?”
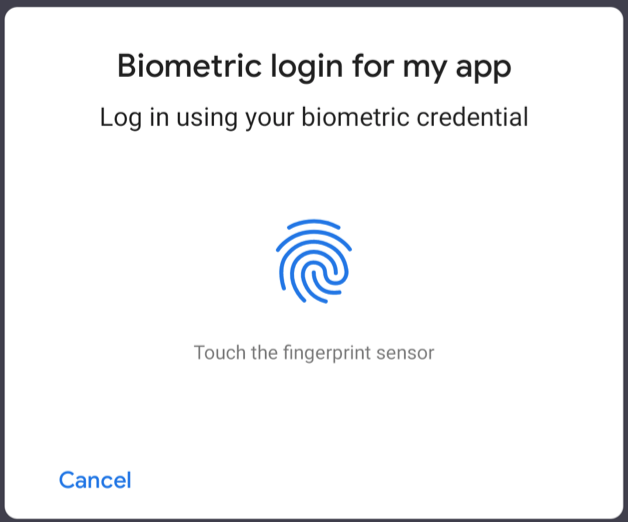
When I’ve demoed “Biometric” UIs to non-developers, many say:
Why don’t you just say “Fingerprint” or “Face Unlock”?
The reason is that the Biometric APIs have no way to find the type of biometric that will be used. That’s why we are stuck with using “Biometric” as a catch all. You can see the terminology being used in Google’s Android Developer Training on Biometric Auth.
We’re also working with the UX / design team on clear iconography/messaging – in the meantime, our suggestion to developers has been to use something along the lines of “Biometric settings”, or “Use biometric”, etc.
– Googler’s Response on Issue Tracker
I have read “BiometricManager” and “BiometricPrompt” enough times to get used to it, but users haven’t. So let’s see what we can do to create better user messaging.
Option A: Describe “What” Instead of “How”
Say what the user is going to do like “Unlock” or “Login” or “Confirm” or whatever. Just don’t mention how the user will do it via a biometric. The system will show the UX for the biometric type anyways in the Biometric Prompt, but your customized wording will be whatever you provide.

Consider these scenarios as well:
- What will you call this on your settings page?

- What iconography will you use for “Biometric” on a Pixel 4 with Face Unlock? A Fingerprint? That’s not ideal.
- How will you encourage your users to use biometrics in your app? Maybe you could say “Unlock Faster Next Time” and it can be implied that a biometric will be used?
You might be able to get away with this messaging, and if you can, congrats! 🎉
Option B: Write Code and Cross Your Fingers🤞
It’s possible to figure out what biometric will be used the majority of the time, and I’ll show you how. 😎
Running on Pixel 3 |
Running on Pixel 4 |
Step 1) See If Device Has Biometric Support
Ask the BiometricManager if it canAuthenticate(), and if it’s successful, or says the user has not enrolled their biometrics, then you know the device is capable.
val biometricManager = BiometricManager.from(context)
val isCapable = when (biometricManager.canAuthenticate()) {
BiometricManager.BIOMETRIC_SUCCESS,
BiometricManager.BIOMETRIC_ERROR_NONE_ENROLLED -> true
else -> false
}
The result of this just tells us that the device is capable of using the BiometricPrompt.
Step 2) Ask PackageManager For Available Features
There are currently only 3 types of Biometrics as of API 29 (Android 10). The Android PackageManager can be queried to see if these features are available on the device.
// Get Package Manager val packageManager : PackageManager = context.packageManager
- Fingerprint (Added in API 23)
val hasFingerprint = packageManager.hasFeature(PackageManager.FEATURE_FINGERPRINT)
- Face (Added in API 29)
val hasFace = packageManager.hasFeature(PackageManager.FEATURE_FACE)
- Iris (Added in API 29)
val hasIris = packageManager.hasFeature(PackageManager.FEATURE_IRIS)
Based on these, you should know, but there are edge cases:
- One is available – If only one is available and the rest are not, you should feel pretty confident that you know the exact type of biometric that will be used.
- More than one available – It is possible that a device could have more than one biometric feature. It could have Face Unlock and Fingerprint. Android is an open platform, and Google has said that OEMs could do this if they choose.
- None are available – If this is the case, and the BiometricManager said you canAuthenticate(), then some sort of biometric is available that we have never seen before. This could be the case if this code is run on a future version of Android with a Biometric type we don’t know about.
Step 3) Determine Supported Biometrics
Based on all the logic above, we will end up with one of the following results.
sealed class Biometrics {
object None : Biometrics()
sealed class Available : Biometrics() {
object Face : Available()
object Fingerprint : Available()
object Iris : Available()
object Multiple : Available()
object Unknown : Available()
}
}
You can then use a “when” statement to create user messaging for a specific biometric hardware type. 🎉
What are future Biometric Types?
We don’t know yet.
Biometric APIs are meant to be more future-looking. We “could” expose something like authenticate(type, info, crypto) etc, but it exposes more API surface and thus has the chance of causing more fragmentation across OEMs.
– Googler’s Response on Issue Tracker
In order to be more open ended, these Biometric APIs are built in a way where generic messaging is the recommended approach currently.
Conflicts with Material Design Guidelines
The Material Design guide for Fingerprint explicitly says to maintain consistency with Android Settings. Such as “Confirm fingerprint”. The BiometricManager tells us if a user “canAuthenticate()“, but doesn’t tell us what types of Biometrics are available on the device or which one (if more than one) is currently enabled. The rationale for this:
If new sensors are developed, we would need to keep updating the “type” list, and apps would also need to keep updating to use the new types. Perhaps there’s a way to make that work, just we haven’t spent much time investigating.
– Googler’s Response on Issue Tracker
I think this is a great way to do it, and aligns with user expectations, but this is not available with current Biometric APIs. 😞
| Pixel 3 Settings |
Pixel 4 Settings |
Conclusion
This all sounds like a lot of work. You can just use “Biometric” and you’ll probably be fine. Users will get used to it eventually, right? No matter how hard we try at this point, we will end up having to use that terminology in the cases where “Multiple” or “Unknown” biometric features are available anyways.
It kinda stinks that we got forced to use these APIs since FingerprintManager is deprecated, and the Biometric APIs have a lot of these little workarounds you may need to do. I understand the rationale behind it from an OS standpoint, but I hope that Google exposes the type(s) of Biometric available on the device to use. That way we are sure, and aren’t doing all this work to try and figure it out.
Recommendations
- Must: Use the AndroidX Library. It’s a wrapper on top of the Android OS APIs and deals with specific workarounds, as well as provides a FingerprintManager fallback for devices prior to API 28 which don’t have a BiometricPrompt in the OS.
- Recommended: Checkout Biometricks which is a library in development to do what is mentioned in this article. It has a sample app and more.
- Recommended: Do some user testing. I’m giving some advice from what I’ve seen, but you may find something different with your users. Your users are your source of truth.
Disclaimers
- This is a UX guide, and not anything related to security of using Biometric features of Android.
- These are my personal observations and opinions.