I’ve seen a few articles about using the “adb reverse” command which allows you to make specific network calls to your laptop over USB, but when explaining this concept to others, they had a hard time visualizing how it worked. I’ve put together this post to help illustrate how this works and spotlight some use cases.
Android’s “adb reverse” command is available in Lollipop and higher versions of Android (Platform 21+) and it allows you to access a server running on your computer from your Android device over USB without any network (WiFi or Cellular). This is done through a technique called a reverse proxy.
What’s a reverse proxy? (via Wikipedia)
A type of proxy server that retrieves resources on behalf of a client from one or more servers. These resources are then returned to the client as though they originated from the proxy server itself.
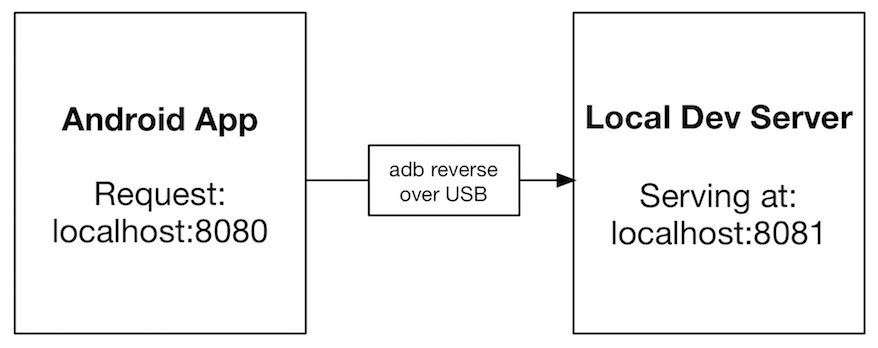
Use Case 1 : Android -> Server running on laptop
Android Device (localhost:8080) -> Server running on Computer (localhost:8081)
adb reverse tcp:8080 tcp:8081
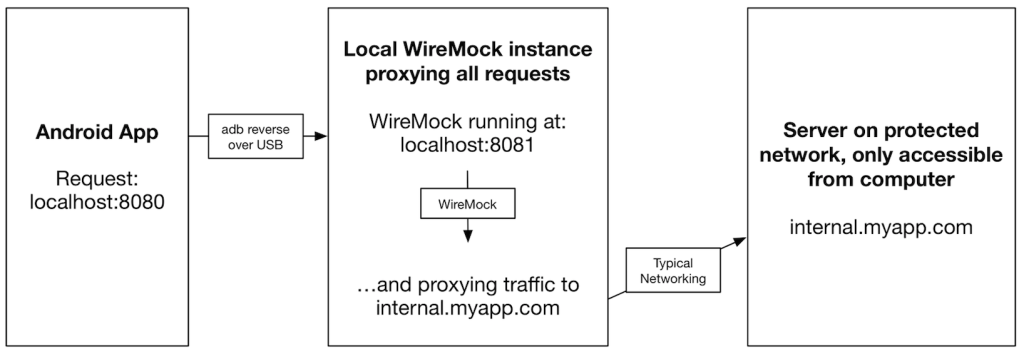
Use Case 2 : Android -> WireMock on laptop -> Server accessible only on laptop (i.e. VPN)
Download the WireMock JAR and run it using the following command in a Terminal
java -jar wiremock-standalone-2.0.8-beta.jar --port=8081 --proxy-all="https://internal.myapp.com"
Android Device (localhost:8080) -> WireMock running on Computer (localhost:8081)
adb reverse tcp:8080 tcp:8081
This allows you to have your physical Android device access resources that are only available through your laptop.
When you’re done, turn off all reverse proxy port mappings:
adb reverse --remove-all
Sources: